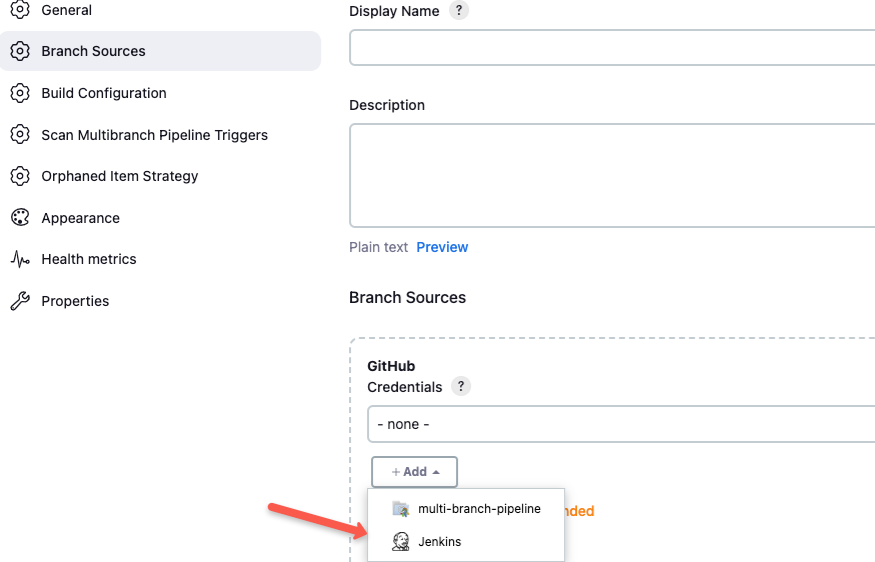
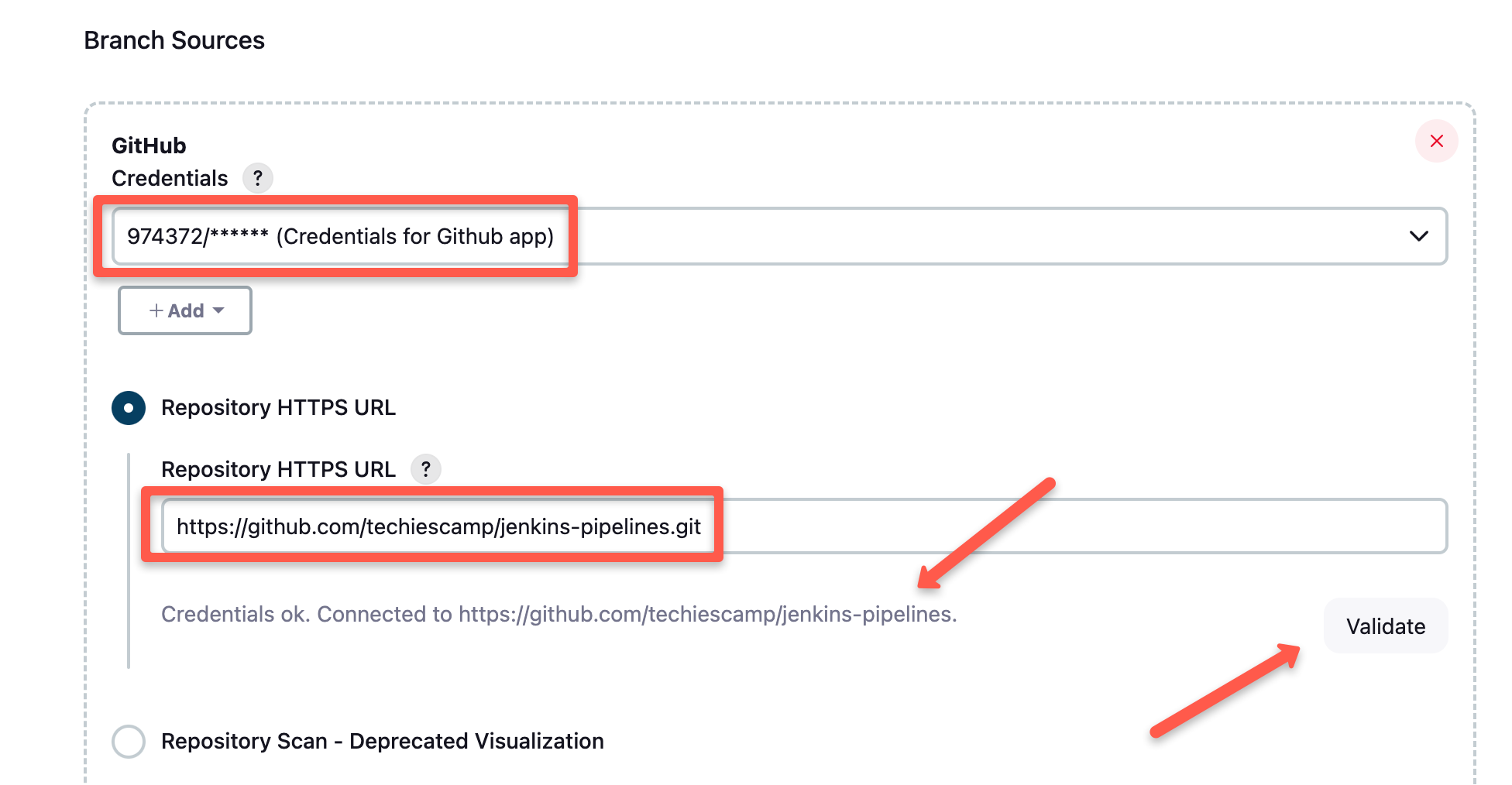
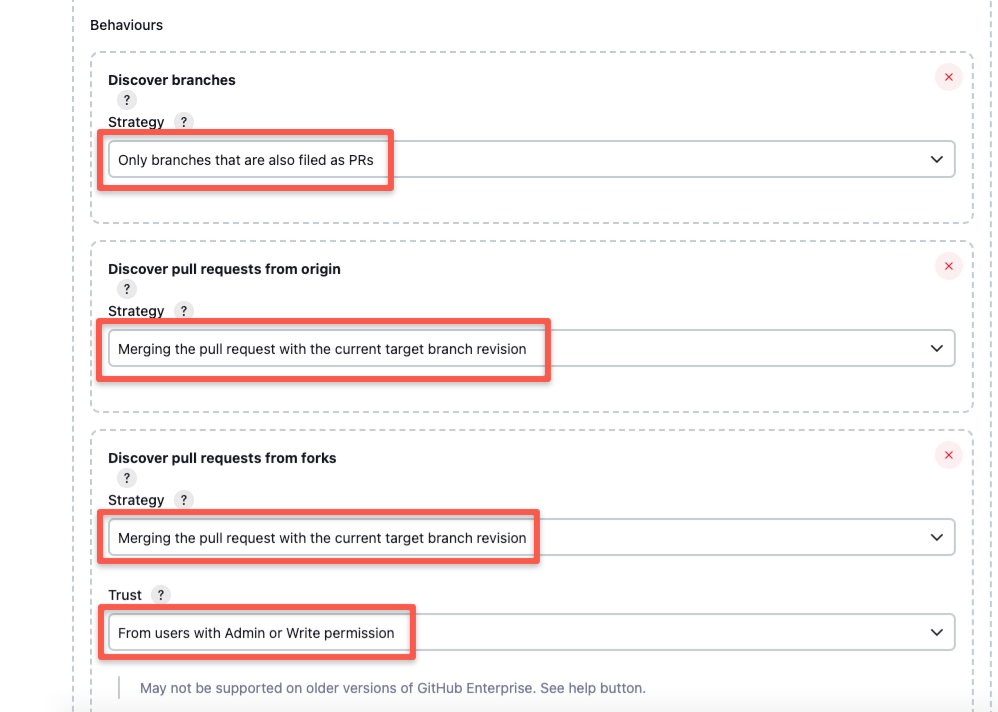
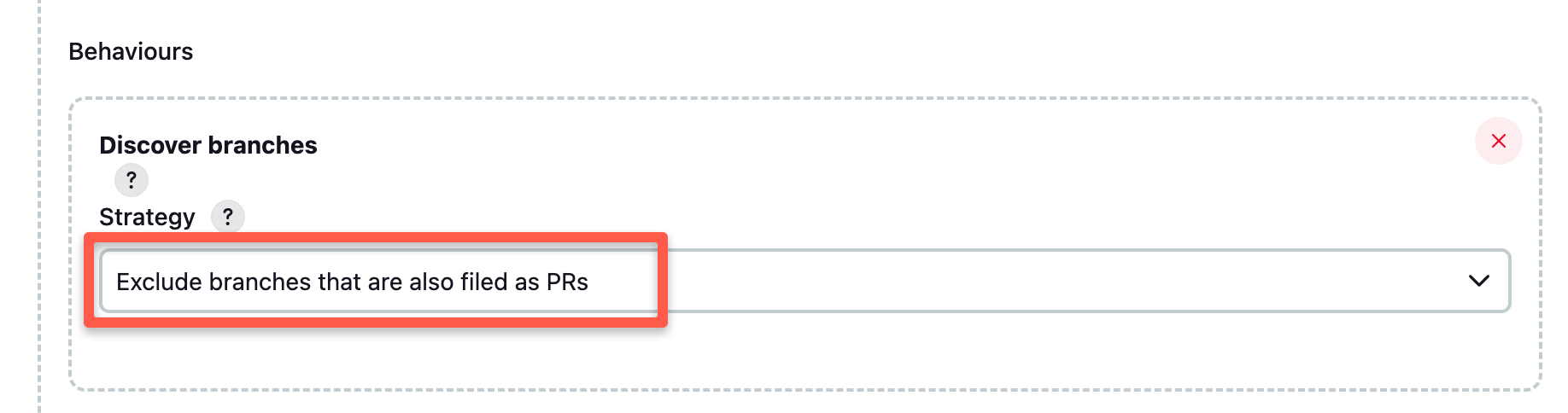
Published on July 19, 2025
The Internet of Things (IoT) is revolutionizing industries by connecting devices, optimizing processes, and enabling data-driven decisions. With 18.8 billion connected devices in 2024, projected to reach 32.1 billion by 2030, IoT’s impact is profound, particularly in semiconductor manufacturing and engineering-related domains like cybersecurity and finance. According to Fortune Business Insights, the global IoT market is expected to grow from $714.48 billion in 2024 to $4,062.34 billion by 2032, with a CAGR of 24.3%. In this article, we explore IoT’s mechanics, benefits, challenges, and real-world applications, with a special focus on semiconductor manufacturing, cybersecurity, and finance case studies, current gaps in solutions, and innovative business ideas to address them. Whether you’re a student, engineer, or entrepreneur, this guide will illuminate IoT’s transformative potential in 2025.
What is IoT?
The Internet of Things (IoT) is a network of physical devices embedded with sensors, software, and connectivity to collect, exchange, and act on data via the internet. These “smart” devices—ranging from industrial sensors to wearables—enable automation, real-time monitoring, and actionable insights. In semiconductor manufacturing and engineering domains, IoT drives efficiency, quality control, and innovation, supported by technologies like AI, 5G, and edge computing.
How Does IoT Work?
IoT systems consist of several key components:
- Devices/Sensors: Hardware like temperature sensors, RFID tags, or vibration sensors that collect data.
- Connectivity: Protocols such as Wi-Fi, 5G, LoRaWAN, or NB-IoT for data transmission.
- Data Processing: Edge computing or cloud platforms (e.g., AWS IoT, Microsoft Azure IoT) for analysis.
- Applications: User interfaces like dashboards or mobile apps for actionable insights.
- Security: Encryption and authentication to protect data and devices.
The architecture typically includes:
- Edge Layer: Sensors collect data (e.g., wafer defects in semiconductor manufacturing).
- Connectivity Layer: Data travels via 5G or LPWAN.
- Processing Layer: Edge or cloud systems analyze data using AI/ML.
- Application Layer: Dashboards deliver insights (e.g., predictive maintenance alerts).
- Security Layer: Ensures data privacy and device integrity.
Why IoT Matters: Benefits and Challenges
Benefits
- Efficiency: Automates processes, reducing manual effort (e.g., IoT sensors optimize semiconductor fab operations).
- Real-Time Insights: Enables proactive decisions (e.g., detecting equipment failures in real-time).
- Cost Savings: Reduces downtime and costs (e.g., Intel cut maintenance costs by 20% using IoT).
- Scalability: Supports growth across devices and applications.
- Sustainability: Optimizes resources (e.g., smart energy systems in fabs reduce waste).
Challenges
- Security: IoT devices faced 1.5 billion cyberattacks in 2021, a critical issue in semiconductor and finance sectors.
- Data Privacy: Compliance with GDPR, PCI-DSS, or other regulations is essential.
- Interoperability: Lack of standard protocols hinders integration across heterogeneous devices.
- Scalability: Managing billions of devices requires robust infrastructure.
- Cost: High initial investment for hardware and platforms.
- Energy Consumption: Devices need efficient power solutions (e.g., energy harvesting).
Real-World IoT Applications: Case Studies from 2024-2025
IoT is transforming industries with tangible results. Below, we highlight case studies across various sectors, with a deeper focus on semiconductor manufacturing, cybersecurity, and finance to showcase their impact and challenges.
Semiconductor Manufacturing
IoT, often referred to as Industrial IoT (IIoT) in this context, enhances semiconductor manufacturing by enabling real-time monitoring, predictive maintenance, and process optimization. The following case studies highlight recent advancements:
- Intel (USA, 2024): Deployed Open Automation Software (OAS) with IoT in 86 fabrication plants, improving equipment uptime by 20% through real-time monitoring and predictive maintenance.
- TSMC (Taiwan, 2024): Used IoT sensors with NVIDIA CUDA-X for ML-based feature engineering, reducing ETL processing time by 40% and enhancing defect detection accuracy in wafer production.
- Siemens AG (Germany, 2024): Advanced IoT with nanotechnology (IoNT) for smart factories, optimizing chip production processes and reducing energy consumption by 15% in semiconductor fabs.
- Samsung Electronics (South Korea, 2024): Implemented IoT for real-time wafer defect detection, improving yield by 25% through AI-driven analytics and sensor networks.
- GlobalFoundries (USA, 2024): Used IoT-enabled predictive maintenance on etching equipment, reducing unplanned downtime by 30% and saving $10 million annually.
Source: Adapted from industry reports and web sources.
Cybersecurity
IoT in cybersecurity enhances threat detection and response but faces challenges due to device vulnerabilities and fragmented systems.
- Intesa Sanpaolo (Italy, 2024): Deployed Microsoft Sentinel with IoT integration to monitor banking IoT devices (e.g., ATMs), reducing fraud detection time by 40%.
- CrowdStrike (USA, 2024): Implemented IoT endpoint detection for industrial IoT devices, reducing ransomware spread by 35% in manufacturing environments.
- Kaspersky (Global, 2024): Used honeypot networks to detect IoT attacks, identifying 100 million attacks from 276,000 unique IP addresses in the first half of 2024.
- Palo Alto Networks (USA, 2024): Deployed IoT security with Zero Trust policies for healthcare IoMT devices, reducing unauthorized access incidents by 30%.
- Armis (USA, 2024): Provided real-time IoT asset visibility for retail IoT networks, cutting vulnerability exploitation by 25% through automated patch management.
Source: Adapted from industry reports and X posts, including @shawnwbailey, July 14, 2025.
Finance
IoT in finance streamlines payment processing, fraud detection, and auditing but struggles with security and compliance challenges.
- JPMorgan Chase (USA, 2024): IoT-enabled mobile POS systems processed contactless payments 30% faster, enhancing customer experience at 5,000+ branches.
- Visa (Global, 2024): IoT wearables for contactless payments increased transaction volume by 20% in urban markets, leveraging secure NFC technology.
- HSBC (UK, 2024): IoT with ML analytics detected fraud in real-time across 1 million+ transactions daily, reducing false positives by 25%.
- Mastercard (Global, 2024): IoT sensors in ATMs tracked performance, reducing downtime by 15% and improving customer access.
- Bank of America (USA, 2024): IoT-enabled audit trails streamlined accounting processes, cutting audit times by 20% through real-time transaction tracking.
Source: Adapted from industry reports and web sources.
Healthcare
- Philips Healthcare (Netherlands, 2024): IoT wearables for remote patient monitoring reduced hospital readmissions by 38% through real-time vitals tracking.
- Medtronic (USA, 2024): IoT-enabled insulin pumps with AI analytics improved diabetes management for 1.2 million patients.
- Apollo Hospitals (India, 2024): IoT telemedicine platforms improved consultations by 40% in rural areas.
- NHS UK (2024): IoT wearables for elderly care reduced emergency visits by 20%.
- Teladoc Health (USA, 2024): IoT telemedicine integration enabled 50% faster diagnoses.
Source: Adapted from industry reports and web sources.
Manufacturing (General Engineering)
- Siemens (Germany, 2024): AIoT predictive maintenance reduced automotive plant downtime by 50%.
- Bosch (Germany, 2024): IoT supply chain tracking improved delivery accuracy by 30%.
- Toyota (Japan, 2024): IoT production monitoring increased assembly line efficiency by 25%.
- Caterpillar (USA, 2024): IoT equipment monitoring cut maintenance costs by 20%.
- Tata Steel (India, 2024): IoT furnace optimization saved $50 million annually.
Source: Adapted from industry reports and web sources.
Agriculture
- John Deere (USA, 2024): IoT precision farming with soil sensors increased crop yields by 20%. EMB Global
- CropX (Israel, 2024): IoT soil monitoring saved 30% water in irrigation.
- Bayer (Germany, 2024): IoT drones for pest monitoring reduced pesticide use by 25%.
- Netafim (Israel, 2024): IoT drip irrigation increased yields by 18% in arid regions.
- Mahindra Agri (India, 2024): IoT weather stations improved planting schedules, boosting yields by 15%.
Source: Adapted from industry reports and web sources.
Smart Cities
- Seoul (South Korea, 2024): AI-powered IoT traffic management reduced congestion by 25%.
- Singapore Smart Nation (2024): IoT smart grids saved 20% energy in public buildings.
- Dubai (UAE, 2024): IoT waste management improved recycling by 30%.
- Toronto (Canada, 2024): IoT parking sensors reduced search time by 40%.
- Barcelona (Spain, 2024): IoT water management cut leaks by 25%.
Source: Adapted from industry reports and web sources.
Retail
- Walmart (USA, 2024): IoT with blockchain for supply chain tracking improved transparency by 35%.
- Amazon (USA, 2024): IoT inventory robots reduced stock errors by 20%.
- Zara (Spain, 2024): IoT RFID tags improved inventory accuracy by 25%.
- Carrefour (France, 2024): IoT smart shelves reduced stockouts by 30%.
- Alibaba (China, 2024): IoT in smart stores improved checkout speed by 22%.
Source: Adapted from industry reports and web sources.
Current Gaps in IoT Solutions for Semiconductor Manufacturing, Cybersecurity, and Finance
Despite IoT’s advancements, significant gaps persist in semiconductor manufacturing, cybersecurity, and finance applications, posing risks and limiting adoption.
Semiconductor Manufacturing Gaps
- Complex Integration: Legacy semiconductor equipment often lacks IoT compatibility, requiring costly retrofitting. Only 30% of fab equipment is IoT-ready.
- Data Overload: IoT sensors generate terabytes of data hourly (e.g., smart vehicles), overwhelming existing analytics systems.
- Security Vulnerabilities: IoT devices in fabs are prone to cyberattacks, as seen in TSMC’s 2018 WannaCry incident, costing $5.2 billion.
- Power Efficiency: IoT chips require ultralow power for edge computing, but current designs struggle to balance performance and efficiency.
- Interoperability: Heterogeneous protocols (e.g., MQTT, OPC UA) hinder seamless integration across fab equipment.
- Scalability: Managing IoT across thousands of sensors in a fab requires robust, vendor-neutral platforms, which are underdeveloped.
- Cost: High costs of IoT-enabled chips (e.g., neuromorphic chips) limit adoption in cost-sensitive applications.
Cybersecurity Gaps
- Resource Constraints: IoT devices lack computational power for advanced encryption, with only 2% supporting modern protocols like PRESENT or CLEFIA.
- Unencrypted Traffic: 98% of IoT device traffic is unencrypted, exposing sensitive data to attacks.
- Weak Authentication: Default passwords and insufficient MFA in 70% of IoT devices enable unauthorized access.
- Patch Management: Outdated firmware in 60% of IoT devices leaves vulnerabilities unpatched.
- Botnet Threats: Over 35% of smart devices are affected by botnet attacks, disrupting networks.
- Lack of Standardization: Heterogeneous protocols create interoperability issues, complicating unified security frameworks.
- Scalability: Centralized security orchestration for billions of devices is inefficient with current solutions.
Finance Gaps
- Regulatory Compliance: IoT devices struggle to meet PCI-DSS or GDPR requirements due to limited processing capabilities.
- Data Privacy: Real-time transaction data from IoT devices (e.g., POS systems) is vulnerable, with 83% of desktop devices lacking IoT threat support.
- Integration Complexity: Legacy financial systems create data silos when integrating with IoT.
- High Costs: Deploying secure IoT infrastructure (e.g., Zero Trust platforms) is expensive for smaller institutions.
- Real-Time Threat Detection: Low-latency anomaly detection across distributed IoT networks is challenging.
- Scalability Challenges: Managing IoT devices across thousands of branches requires robust platforms.
Market Trends Shaping IoT in 2025
IoT is evolving rapidly, driven by technological advancements and market demands. Key trends include:
- Market Growth: The IoT market is expected to reach $1.5 trillion by 2024 and $3.3 trillion by 2030, with a CAGR of 24.3%. Fortune Business Insights
- Device Proliferation: 18.8 billion connected devices in 2024, projected to hit 27 billion by 2025. ValueCoders
- 5G and Wi-Fi 7: Enable faster, low-latency connectivity for real-time applications.
- Edge Computing: Processes data locally, reducing latency; market to reach $274 billion by 2025.
- AIoT: Combines AI with IoT for predictive analytics (e.g., defect detection in semiconductors).
- Blockchain Integration: Enhances IoT data security (e.g., secure transactions in finance).
- Sustainability: IoT supports ESG goals by optimizing resources (e.g., energy management in fabs).
According to IoT Analytics, 92% of enterprises reported positive ROI from IoT projects in 2024, with a 53% increase in use case adoption since 2021.
Innovative IoT Business Ideas for 2025
To address the gaps in semiconductor manufacturing, cybersecurity, and finance, below are innovative business ideas tailored to these domains, alongside ideas for other engineering-related sectors.
Semiconductor Manufacturing
Challenge: Complex integration, data overload, security vulnerabilities.
- IoT-Ready Fab Retrofit Kit: Develops plug-and-play IoT modules for legacy equipment, enabling real-time monitoring. Impact: Increases IoT adoption by 30%.
- AIoT Defect Detection Platform: Uses SemiKong and edge computing for real-time wafer defect analysis. Impact: Improves yield by 25%.
- Low-Power IoT Chip Design: Creates energy-efficient chips for edge computing in fabs. Impact: Reduces power consumption by 20%.
- Blockchain-IoT Supply Chain Tracker: Secures chip supply chain data with blockchain. Impact: Improves transparency by 30%.
- Vendor-Neutral IoT Protocol Hub: Standardizes protocols (e.g., MQTT, OPC UA) for fab interoperability. Impact: Enhances integration by 25%.
- IoT Data Compression Tool: Compresses terabyte-scale fab data for efficient analytics. Impact: Reduces processing time by 40%.
- Secure IoT Fab Gateway: Implements Zero Trust security for fab IoT devices. Impact: Cuts cyberattack risks by 30%.
- Predictive Maintenance IoT Suite: Uses digital twins for equipment failure prediction. Impact: Reduces downtime by 35%.
- IoT Energy Management System: Optimizes fab energy use with AI-driven sensors. Impact: Saves 15% energy costs.
- Nanotech IoT Sensors: Deploys IoNT sensors for ultra-precise chip monitoring. Impact: Improves quality control by 20%.
Cybersecurity
Challenge: Resource constraints, unencrypted traffic, botnet vulnerabilities.
- Lightweight Cryptographic IoT Suite: Develops low-power encryption protocols (e.g., PRESENT) for IoT devices. Impact: Secures 50% more devices.
- AI-Driven IoT Threat Detection: Uses ML to detect anomalies in real-time. Impact: Reduces attack response time by 40%.
- Blockchain-IoT Authentication Platform: Implements decentralized authentication to replace weak passwords. Impact: Cuts unauthorized access by 30%.
- Automated Patch Management IoT Tool: Centralizes firmware updates for IoT devices. Impact: Reduces vulnerabilities by 35%.
- Zero Trust IoT Orchestration: Deploys vendor-neutral Zero Trust policies. Impact: Lowers breach risks by 25%.
- IoT Honeypot Network: Detects and analyzes attacks to improve threat intelligence. Impact: Identifies 20% more attack patterns.
- Edge-Based Intrusion Detection System: Processes security data locally. Impact: Cuts detection time by 30%.
- IoT Security-by-Design Framework: Embeds security in device development. Impact: Reduces vulnerabilities by 25%.
- MFA IoT Gateway: Enforces multi-factor authentication for IoT access. Impact: Reduces unauthorized access by 20%.
- Botnet-Resistant IoT Protocol: Isolates compromised devices to mitigate attacks. Impact: Mitigates botnet attacks by 35%.
Finance
Challenge: Compliance, privacy, integration issues.
- PCI-DSS Compliant IoT POS System: Ensures secure, compliant payment processing. Impact: Reduces compliance violations by 30%.
- Blockchain-IoT Transaction Tracker: Secures transaction data with blockchain. Impact: Improves transparency by 25%.
- IoT Fraud Detection Wearables: Uses wearables for biometric verification. Impact: Cuts fraud by 20%.
- Real-Time IoT Audit Platform: Automates audit trails for transactions. Impact: Reduces audit times by 25%.
- Vendor-Neutral IoT Integration Hub: Connects legacy systems with IoT devices. Impact: Improves efficiency by 20%.
- AIoT Anomaly Detection for ATMs: Monitors ATM performance and fraud. Impact: Reduces downtime by 15%.
- Secure IoT Payment Gateway: Uses ECC and PUFs for encryption. Impact: Cuts data breaches by 20%.
- IoT Customer Analytics Platform: Tracks behavior securely via IoT devices. Impact: Boosts sales by 15%.
- Energy-Efficient IoT Sensors for Finance: Reduces power consumption in branch networks. Impact: Cuts costs by 20%.
- Decentralized IoT Banking App: Uses SDN for secure, scalable services. Impact: Enhances uptime by 25%.
Healthcare
Challenge: Inefficient monitoring, high costs, data security.
- AIoT Telehealth Platform: Integrates wearables with AI and blockchain. Impact: Reduces readmissions by 30%.
- Smart Hospital Bed System: IoT beds monitor vitals and adjust positions. Impact: Saves 20% staff time.
- IoT Medication Adherence Device: Alerts caregivers for missed doses. Impact: Increases adherence by 25%.
- Wearable Mental Health Monitor: Tracks stress for early intervention. Impact: Reduces crises by 15%.
- IoT Surgical Robotics: Enables precision surgery with real-time feedback. Impact: Improves outcomes by 20%.
Manufacturing (General Engineering)
Challenge: Downtime, supply chain inefficiencies, energy costs.
- AIoT Predictive Maintenance Suite: Uses digital twins for failure prediction. Impact: Reduces downtime by 50%.
- Blockchain-IoT Supply Chain Tracker: Ensures transparent tracking with RFID. Impact: Improves delivery accuracy by 30%.
- Smart Energy Management System: Optimizes factory energy use. Impact: Saves 20% energy costs.
- IoT Quality Control Drones: Detects production defects. Impact: Reduces defects by 25%.
- 5G-Enabled IoT Robotics: Enhances factory automation. Impact: Boosts production speed by 20%.
Agriculture
Challenge: Resource waste, low yields, environmental impact.
- IoT Precision Irrigation System: Solar-powered sensors optimize water use. Impact: Saves 30% water.
- Drone-Based IoT Crop Monitoring: Detects pests, reducing chemical use. Impact: Cuts pesticide costs by 25%.
- IoT Livestock Health Tracker: Monitors health, reducing mortality. Impact: Saves 15% livestock losses.
- Smart Greenhouse IoT: Controls temperature and humidity. Impact: Boosts yields by 20%.
- IoT Weather Prediction System: Improves planting schedules. Impact: Increases yields by 15%.
Smart Cities
Challenge: Traffic congestion, energy waste, public safety.
- AIoT Traffic Management System: Optimizes traffic light timing. Impact: Reduces congestion by 25%.
- Smart Grid IoT Network: Manages energy distribution. Impact: Saves 20% energy.
- IoT Waste Management System: Optimizes collection routes. Impact: Reduces costs by 30%.
- IoT Public Safety Cameras: Enhances incident detection. Impact: Improves response times by 20%.
- Smart Lighting IoT: Adjusts brightness based on occupancy. Impact: Saves 15% energy.
Retail
Challenge: Inventory mismanagement, poor customer experience.
- IoT Smart Shelves: Monitors stock levels in real-time. Impact: Reduces stockouts by 30%.
- IoT Customer Analytics: Beacons enable personalized offers. Impact: Boosts sales by 15%.
- Blockchain-IoT Supply Chain: Ensures transparent tracking. Impact: Improves delivery accuracy by 25%.
- IoT Smart Checkout: Speeds up transactions with AI. Impact: Reduces checkout time by 20%.
- IoT Food Safety Sensors: Ensures perishable goods compliance. Impact: Reduces spoilage by 20%.
The Future of IoT: Opportunities and Considerations
IoT’s potential is vast, but addressing challenges is critical:
- Security: Implement encryption, Zero Trust, and AI-based threat detection to combat cyberattacks.
- Interoperability: Adopt standards like MQTT or OPC UA for seamless integration.
- Privacy: Ensure compliance with GDPR, PCI-DSS, and other regulations.
- Scalability: Invest in robust cloud and edge infrastructure.
- Sustainability: Use energy-harvesting devices to reduce environmental impact.
By addressing these gaps, businesses can unlock IoT’s full potential, creating smarter, more secure, and sustainable operations in semiconductor manufacturing and engineering domains.
Conclusion
IoT is transforming industries by connecting devices and enabling data-driven decisions. From optimizing semiconductor fabs to securing financial transactions, its impact is undeniable. However, challenges like integration complexity, security vulnerabilities, and compliance issues must be addressed. By leveraging innovative solutions like AIoT, blockchain, and standardized protocols, businesses can stay ahead in the connected world of 2025. What’s your favorite IoT application? Share your thoughts in the comments below!
References
- Fortune Business Insights. (2022). Internet of Things [IoT] Market Size, Share, Growth, Trends, 2032. www.fortunebusinessinsights.com
- ValueCoders. (2024). Exploring 2025's Top 10 IoT Use Cases: Insights & Statistics. www.valuecoders.com
- IoT Analytics. (2024). IoT Use Case Adoption Report 2024. iot-analytics.com
- EMB Global. (2024). The Most Impactful IoT Case Studies of the Decade. blog.emb.global